Guest collaboration is a powerful strategy for enabling secure business-to-business engagements between Microsoft Entra ID tenants without the need to provision credentials for partner users. Microsoft heavily leverages this guest mechanism for services like Teams, SharePoint, OneDrive, and Office 365, which can lead to a rapid accumulation of guest accounts in your tenant. However, there's no simple built-in mechanism to decommission these accounts when they're no longer needed. Maintaining a clean tenant by removing stale guest accounts is crucial for your Identity and Access Management (IAM) security posture.
In this article, we'll explore how to automate the de-provisioning of guest accounts using Apporetum Identity State Model (ISM) with basic rules and actions. We'll implement a strategy to disable accounts after 90 days of inactivity and delete them after 120 days. This approach allows guest users to request renewed access to the tenant after a reasonable period without losing their existing permissions. Additionally, we'll demonstrate how to harvest all entitlements associated with these accounts and send email notifications to users, informing them how to reactivate their accounts if needed. This B2B Modern Cloud IAM architecture allows you to leverage your ROI in the Microsoft Entra ID and minimise the amount of scripting that you need to do in your environment to get the business outcomes you need for your security requirements.
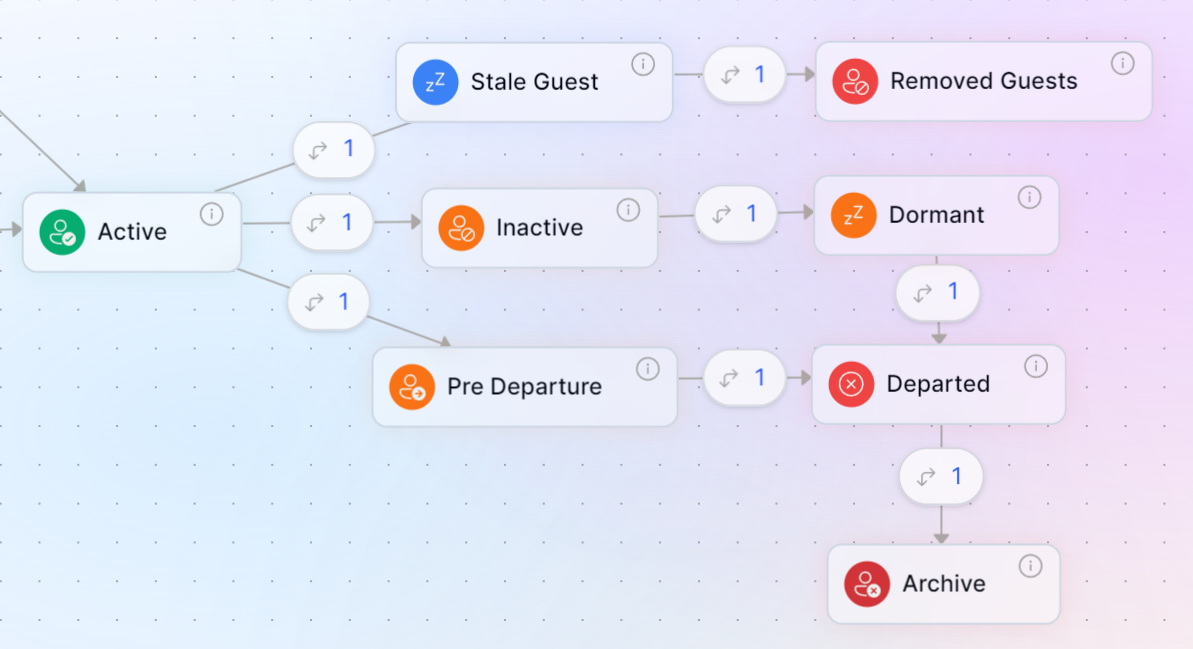
Offboarding Inactive Guest Users via Apporetum Identity State Models
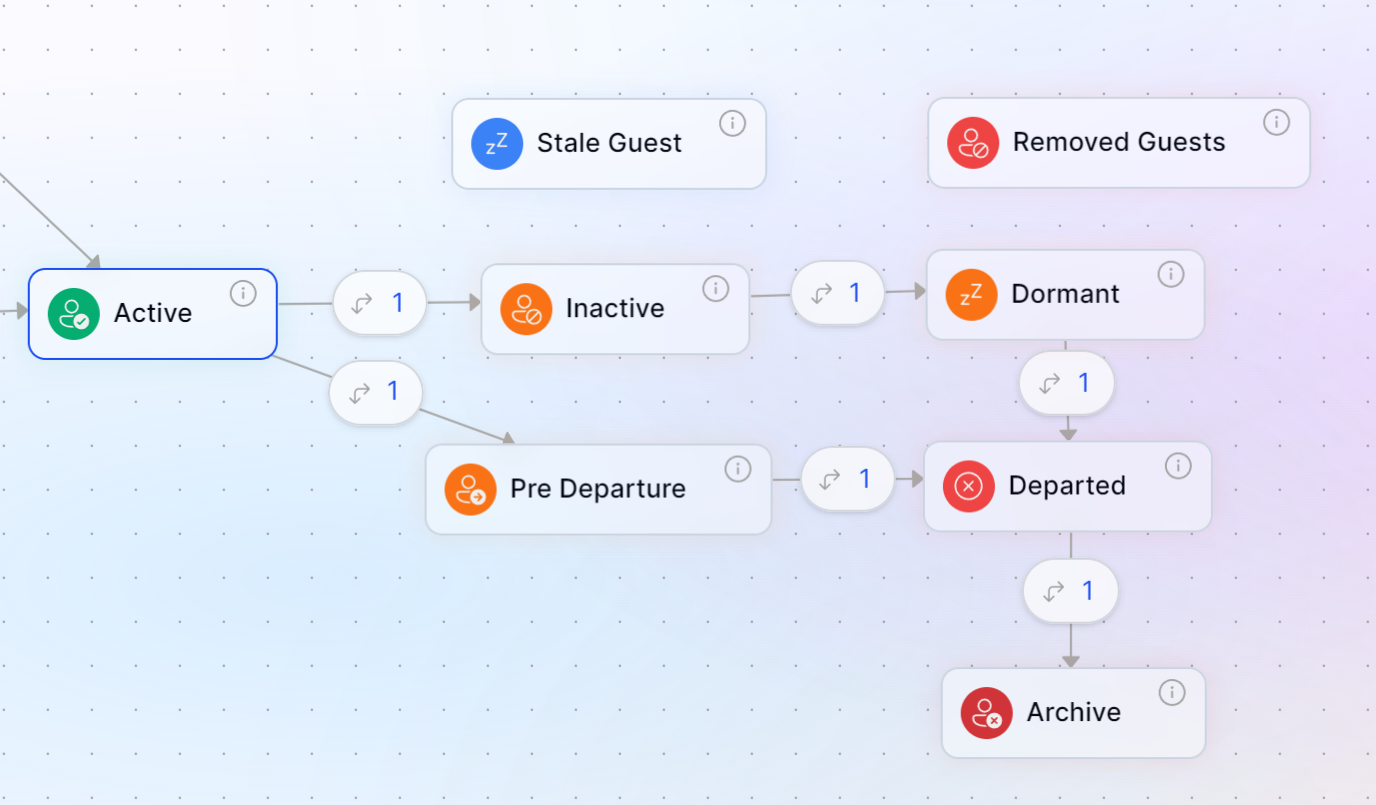
We're planning to implement two new states for guest user offboarding, transitioning from the "Active" state. These are:
- "Stale Guest": This state will include all guest accounts that have shown no activity for 90 days or longer.
- "Removed Guests": This state will encompass all "Stale Guest" accounts that have remained inactive for 120 days or more.
These new states will help manage the lifecycle of guest user accounts based on their inactivity periods.
Move Stale Guest Accounts Users In Entra ID
First, we must add a new transition which will allow guest user accounts to move from the "active" or general state to a stale state. We do this by adding in a trigger which finds guest accounts which have not been used in our directory for the past 90 days.
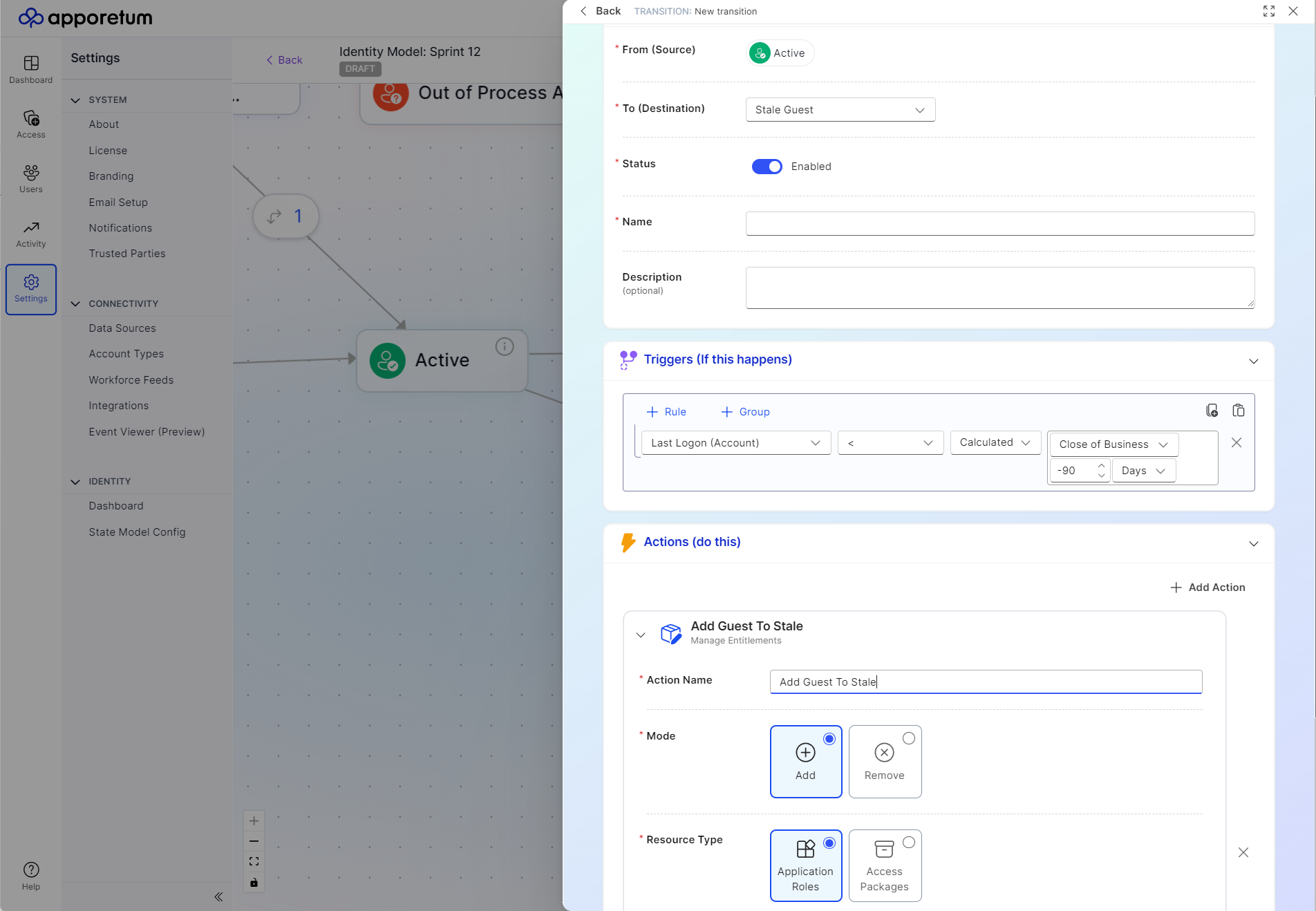
Now, once a guest has been identified, we need to move the guest accounts to the correct states when they become stale and disable their access into our tenant.
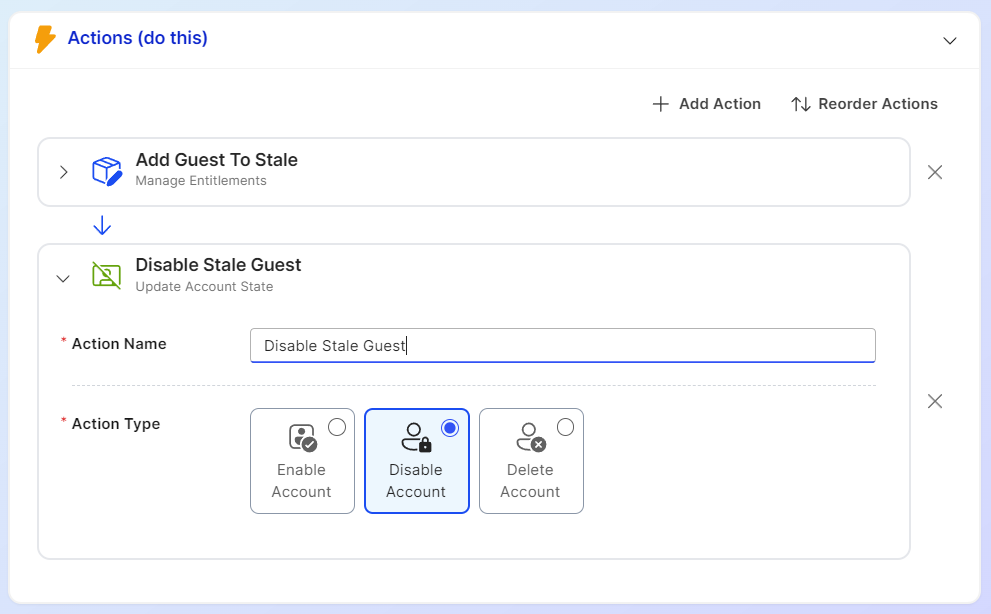
Apporetum's ISM State Actions allow us to manage user accounts through disabling, deleting, or enabling them. Our proposed lifecycle management strategy is as follows:
- After 90 days of inactivity, disable the user account.
- Following an additional 90-day period, delete the account if it remains unused.
This approach provides a 180-day grace period to verify the account's inactive status before permanent deletion. To exclude certain accounts from this automated lifecycle management:
- Implement a whitelist system for guest accounts.
- Use account types or specific properties to identify accounts that should be exempt.
For instance, we can whitelist auditing accounts that are used quarterly, ensuring they aren't subject to the standard lifecycle management process. This system allows for efficient account management while maintaining flexibility for special-case accounts. An example of this is auditing accounts which are used on a quarterly basis to not be lifecycle managed.
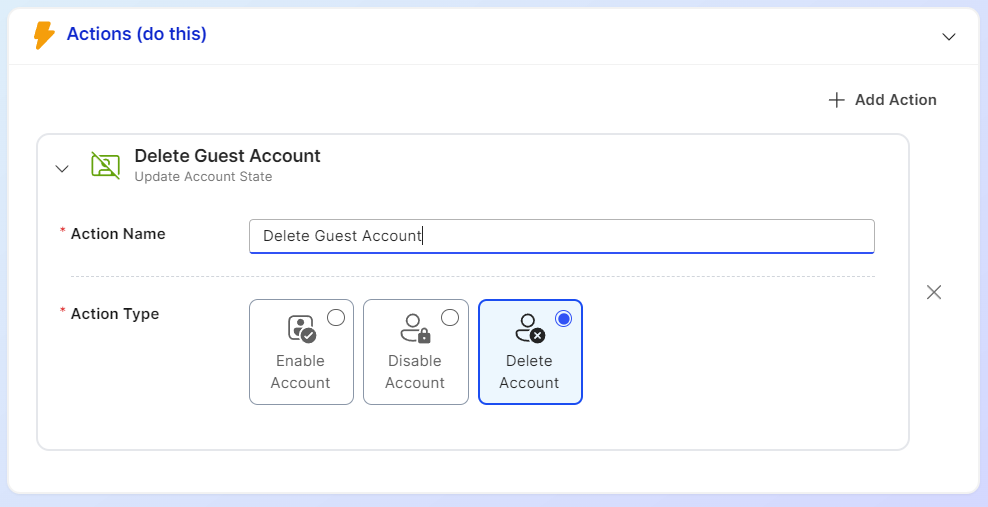
Delete Expired Stale Guest Accounts
We can create an almost identical transition to delete these accounts after they have been inactive for 180 days. Like before, we use the "Update Account Status" action, but we instead use the delete function to remove the account from our directory.
Our final identity state model has a clear channel for offboarding guest user accounts from our Microsoft Entra ID and Microsoft Entra External ID. We can now drive reports to see when their accounts will be off-boarded and how many guest accounts have been cleaned up.
One final feature we can add is the ability to harvest entitlements before we delete the account so that we can quickly restore access to the guest B2B user account before we delete it. This gives Apporetum a snapshot to then restore all the groups to the user object if it needs to be restored.
Leveraging Apporetum Access Reviews
Now that we have all our expiring guest accounts in a group or state we can set up an Application in Apporetum to run B2B account governance access reviews. We can either use Dynamic Guardrails which will automatically control the members or add users automatically via the ISM to control access reviews.
Here's a rewrite of the text: By assigning managers to guest users upon creation, we can enhance our review process. If we implement controls on channel access for guest users within our organisations, we can manage the manager field on each account. This approach allows us to leverage Apporetum's One-Up IAM Access Reviews, enabling access reviews by individuals who understand the rationale and method behind each B2B account's creation.
Conclusion
Managing external account access in your environment requires careful and dedicated oversight to ensure inactive guest users are properly handled. Controlling the channels through which guest accounts are onboarded into your system is one effective way to mitigate security risks. However, in our increasingly interconnected world, maintaining control over guest user accounts has become more challenging than ever.
Apporetum offers a solution that significantly reduces the strain on your business by automating the offboarding process for stale guest accounts using Guest B2B Identity Governance using Apporetum Identity State Model. This proactive approach enhances your security posture while freeing up valuable resources.
If you're interested in discovering how Apporetum can bolster your Guest B2B Identity Governance using our innovative Identity State Model for lifecycle management, we're here to help. Alternatively, why not book a demo with one of our team to see our solution in action