

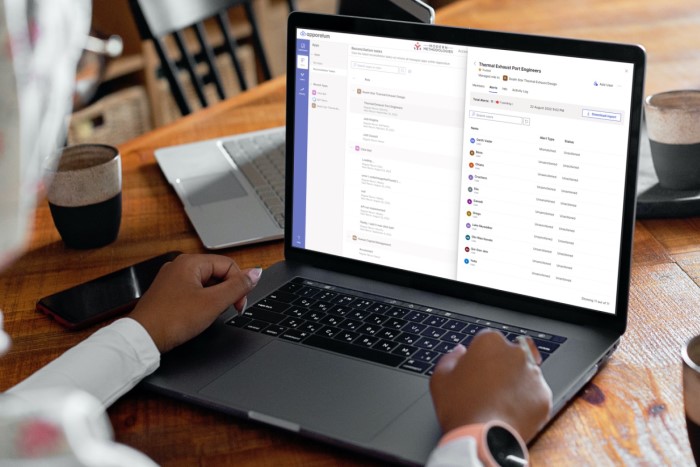
As Apporetum becomes a Source of Authority for all entitlements for your applications, it can detect when an unsanctioned entitlement appears.
Apporetum conducts a reconciliation process (at scheduled intervals) to see if there are entitlements in your directories that have not been provisioned through Apporetum. This process detects unsanctioned entitlements and raises flags so that your Security Team can investigate.
How your organisation responds to unsanctioned entitlements will probably be dictated by the nature of the unsanctioned entitlement – a right fit for risk approach is normally the best. Apporetum enables you to temporarily suspend entitlements while your Security Team investigates. These entitlements can then be restored or removed, as appropriate.


Apporteum keeps a full audit log of all entitlements that are provisioned and deprovisioned so you can track suspicious behaviours, such as granting entitlements for a very short period of time. For example, you can query Apporetum’s logs to see if ‘any entitlements existed for just 24 hours’. This sort of access can remain undetected by normal access review regimes that just look at compliance at a ‘point in time’.
Find answers to commonly asked questions about Apporetum Access Manager
An ‘unsanctioned entitlement’ is access granted outside of the approved process within Apporetum.
Apporetum looks for users who have been provisioned with an entitlement that has not been granted through the Apporetum process. These entitlements may be genuine (for example, an entitlement granted by a Service Desk personnel with appropriate authorisation), or may be suspicious (granted manually directly in the directory without authorisation). Your Security Team will undertake the necessary investigation to determine what the correct response is.
Apporetum allows the reconciliation interval to be set by the application owner. The reconciliation interval reflects how sensitive the role is. The more sensitive the role, the more frequent the reconciliation process.
